As marketers and sales professionals strive to maximize the impact of their campaigns in an increasingly competitive digital ecosystem, email authentication emerges as an essential pillar of success. By prioritizing and implementing robust authentication protocols, marketers can safeguard their brand’s reputation, foster customer trust, and unlock the full potential of email marketing as a powerful business growth driver.
DMARC, DKIM, and SPF are three primary email security protocols that help combat spam, phishing, and other email-based attacks. In this guide, we will explain these three main email security protocols, how they work, and how you can use them to improve email deliverability.
- What Is SPF?
- How Does SPF Work?
- What Is DKIM?
- How Does DKIM Work?
- What Is DMARC?
- How Does DMARC Work?
- Why You Need DMARC, SPF and DKIM
- Protecting Brand Reputation
- Improved Deliverability
- Compliance
- Data Insights
- How Do SPF, DKIM, and DMARC Work Together?
- Where Are SPF, DKIM, and DMARC Records Stored?
- How to Check if an Email Has Passed SPF, DKIM, and DMARC
- Setting up DMARC, DKIM, and SPF for a Domain
- How to Set Up SPF
- How to Set Up DKIM
- How to Set Up DMARC Record
- Use a Separate Domain for Cold Email Outreach
What Is SPF?
Sender Policy Framework (SPF) is an email authentication protocol that helps verify that an email message was sent from an authorized server. It works by checking the DNS records of the sender’s domain to ensure that the sending server has been granted authorization to send emails on behalf of the domain.
How Does SPF Work?
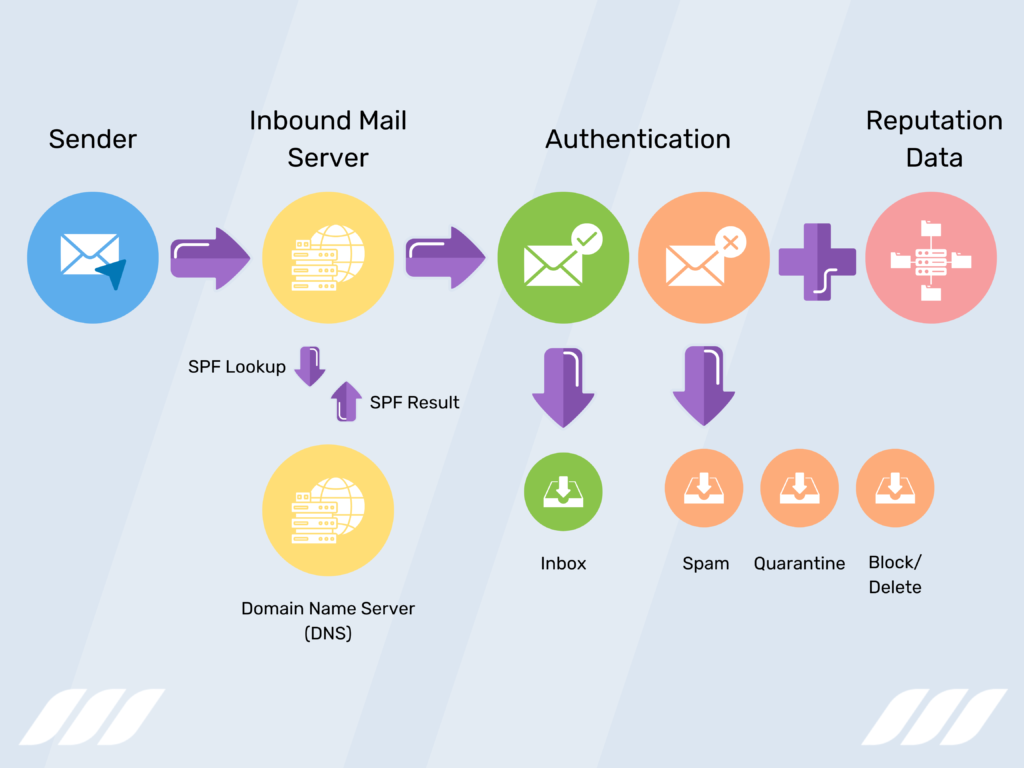
Sender Policy Framework works by adding a TXT record to the DNS settings of a domain. This record specifies which servers are authorized to send email from that domain. When an email is received, the recipient server checks the SPF record of the sender’s domain to confirm that the server sending the message is allowed to send mail on behalf of that domain.
For example, let’s say your company uses the domain example.com. Plus, it uses a third-party email service provider to send emails. In that case, you would need to add an SPF record to your DNS settings to authorize your email provider’s servers to send emails on behalf of your domain. This record would typically look something like this:
v=spf1 include:emailprovider.com ~all
This record specifies that only servers belonging to emailprovider.com are authorized to send email on behalf of example.com. The “~all” parameter indicates that if a server is not authorized, the email should still be accepted but marked as potentially suspicious.
Here’s another example of how an SPF record looks like:
v=spf1 a mx ip4:192.168.0.1/24 include:_spf.google.com ~all
This SPF record authorizes the IP address range 192.168.0.1/24, the A record, and the MX record to send email for the domain. The record also includes the Google mail servers as authorized senders, and any other sender that passes the SPF check will be treated as a soft fail (~all).
What Is DKIM?
DomainKeys Identified Mail (DKIM) is another email authentication protocol that helps verify the authenticity of an email message. Unlike SPF, which verifies the sending server’s authorization, DKIM verifies the email’s content’s integrity. It does so by adding a digital signature to the email header, which the recipient server can verify.
How Does DKIM Work?
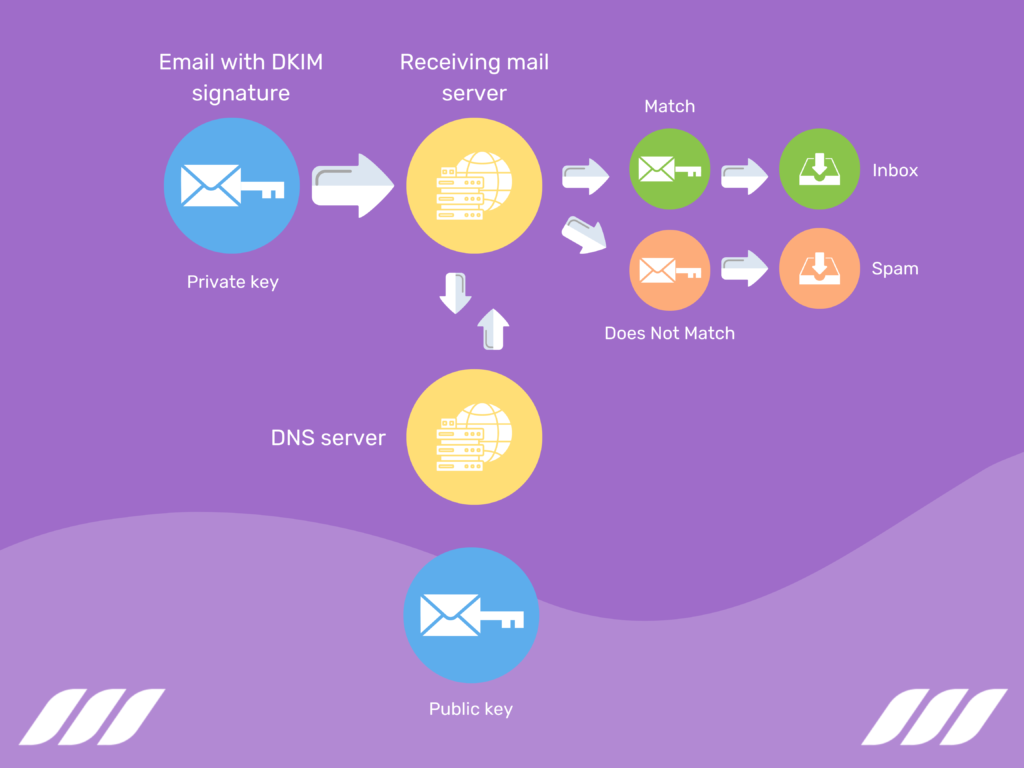
Domainkeys Identified Mail works by adding a digital signature to the email header. The signature is generated through a private key that only the sending server knows. The signature is added to the email header, along with a public key that the recipient server can use to verify the signature’s authenticity.
When the recipient server receives the email, it checks the DKIM signature by using the public key in the email header to decrypt the signature. If the signature matches the email’s content, the email is considered authentic.
DKIM helps the receiver to confirm that the message has not been altered or tampered with during transit. This is because the digital signature is calculated based on the email message’s content. If any part of the email message changes, the digital signature will become invalid, and the email will be rejected.
What’s more, DKIM provides a way for email receivers to identify the domain of the email sender. This provides a defense against phishing emails, as email receivers can use this information to determine whether an email is from a legitimate sender.
Here’s an example to help you understand how DKIM works:
Let’s say you’re a marketing manager at a large e-commerce company, and you want to send promotional emails to your customers. You create a campaign and use your company’s email service provider to send the emails.
Your company has implemented DKIM, so the email service provider adds a unique digital signature to each email using a private key. When the recipient’s email provider receives the email, it checks the public key in your company’s DNS records to verify the signature. If the signature is valid, the message is delivered to the recipient’s inbox, and if not, it’s marked as spam.
What Is DMARC?
Domain-Based Message Authentication, Reporting & Conformance (DMARC) is a protocol that works with SPF and DKIM to provide a more robust email authentication system.
DMARC allows domain owners to publish policies that specify what should happen to emails that fail authentication checks. It provides a way for email receivers to determine whether incoming emails are authentic and to specify how to handle emails that fail authentication.
How Does DMARC Work?
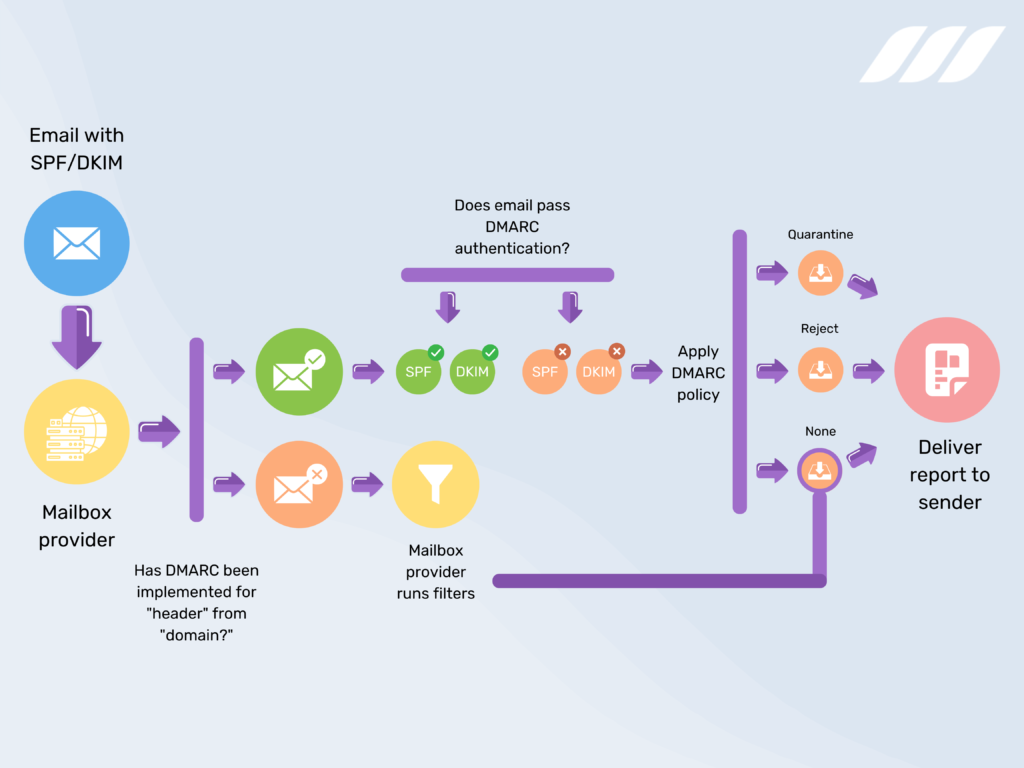
Domain-based Message Authentication, Reporting & Conformance works by adding a TXT record to the DNS settings of a domain that specifies how to handle failed SPF and DKIM checks. It starts by checking the alignment of the domain specified in the From header of the email with the domains specified in the DKIM and SPF records. If these domains do not align, it suggests that the email may have been spoofed and should be rejected or marked as spam.
When an email is received, the recipient’s server checks the SPF and DKIM records to determine whether the email is authentic. If either record fails, the email is marked as spam or rejected, depending on the policies set by the recipient’s email server.
And if the email passes the SPF and DKIM checks, the recipient’s email server checks for a DMARC policy in the DNS records for the sender’s domain. This policy specifies how the recipient’s email server should handle the email if it fails the DMARC check.
The DMARC record can specify one of three actions to take:
- None: Take no action.
- Quarantine: Mark the email as potentially suspicious and place it in the recipient’s spam or junk folder.
- Reject: Reject the email outright and do not deliver it to the recipient.
The DMARC record also specifies how often the recipient server should send reports back to the domain owner about emails that fail authentication checks.
Here’s an example to help you understand how DMARC works:
Suppose ABC company uses a separate domain for cold emailing. The company can implement DMARC on its primary domain to protect its brand reputation and prevent unauthorized use of its domain. The DMARC record specifies that any email claiming to be from the company’s primary domain must pass SPF and DKIM authentication checks, and if an email fails these checks, it should be rejected or marked as spam.
When a recipient’s email provider receives an email claiming to be from the ABC company’s primary domain, it checks the SPF and DKIM authentication results against the DMARC policy. If the email passes both authentication checks, it is delivered to the recipient’s inbox. If it fails, the email is either rejected or marked as spam, protecting the company’s brand reputation and preventing unauthorized use of its domain for phishing or spamming.
Why You Need DMARC, SPF and DKIM
Implementing DMARC, SPF and DKIM provides a robust defense against email problems, including spam, phishing, and operator error. The best part? These protocols help you protect your brand reputation, prevent email fraud, and improve email deliverability.
Here are some of the benefits of each protocol for email marketers and companies:
Protecting Brand Reputation
DMARC, SPF, and DKIM can help protect your brand reputation by preventing email fraud and phishing attacks. By authenticating your email messages, you can ensure that your customers receive only legitimate emails from your organization. This helps build trust with your customers and ensures that your brand reputation is not tarnished by fraudulent emails.
Improved Deliverability
Implementing DMARC, SPF, and DKIM can also improve email deliverability by reducing the chances of your emails being marked as spam or being blocked by email providers. By authenticating your emails, you can establish trust with email providers, who will then be more likely to deliver your emails to your leads’ or customers’ inboxes.
Compliance
Most industries today are required to comply with various regulatory requirements and guidelines, such as HIPAA or GDPR, that require organizations to implement appropriate measures to secure sensitive data. DMARC, SPF, and DKIM are critical measures to comply with these regulations by ensuring that email messages containing sensitive information are securely delivered to the intended recipient.
Data Insights
DMARC, SPF and DKIM also provide valuable data insights into your email delivery and engagement metrics. DMARC reports provide information about your email authentication status and help identify potential issues with email authentication. These insights can help businesses improve their email deliverability and engagement rates, resulting in better ROI.
How Do SPF, DKIM, and DMARC Work Together?
SPF, DKIM, and DMARC work together to provide a more robust email authentication system.
Here’s how they work in tandem:
- SPF verifies that the sending server is authorized to send email from the sender’s domain.
- DKIM verifies the integrity of the email’s content and ensures that the email has not been tampered with in transit.
- DMARC specifies how to handle failed authentication checks and provides a way for domain owners to receive reports about failed authentication attempts.
As you can see, SPF and DKIM use different methods to verify the authenticity of an email message. When an email is received, the recipient’s email provider checks the SPF and DKIM authentication results against the DMARC policy. And since DMARC builds on SPF and DKIM, it empowers domain owners to decide how to handle email messages that fail authentication checks, such as rejecting or quarantining them.
By implementing all three protocols, you can help ensure your emails are delivered into your audiences’ inboxes. That’s not all; using these protocols together helps build trust with your target audience and protect your reputation.
However, it’s important to note that implementing these protocols requires technical expertise and careful planning. It is a good idea to work with your IT team or email service provider to properly set up and configure these protocols to ensure their effectiveness.
Where Are SPF, DKIM, and DMARC Records Stored?
SPF, DKIM, and DMARC records are stored in the DNS settings of the sender’s domain.
DNS records are like a phone book for the internet, providing information about how to find and connect to a domain’s servers. SPF, DKIM, and DMARC records are added to the DNS records for the domain that is sending the email.
When an email is received, the recipient’s email server will look up the domain’s DNS records to find the SPF, DKIM, and DMARC records. But it’s important to note that each domain can only have one SPF record, but multiple DKIM and DMARC records can be added.
SPF, DKIM, and DMARC records should be carefully configured and tested to ensure they work correctly. Any errors or misconfigurations can result in emails being marked as spam or being rejected by the recipient’s email server.
How to Check if an Email Has Passed SPF, DKIM, and DMARC
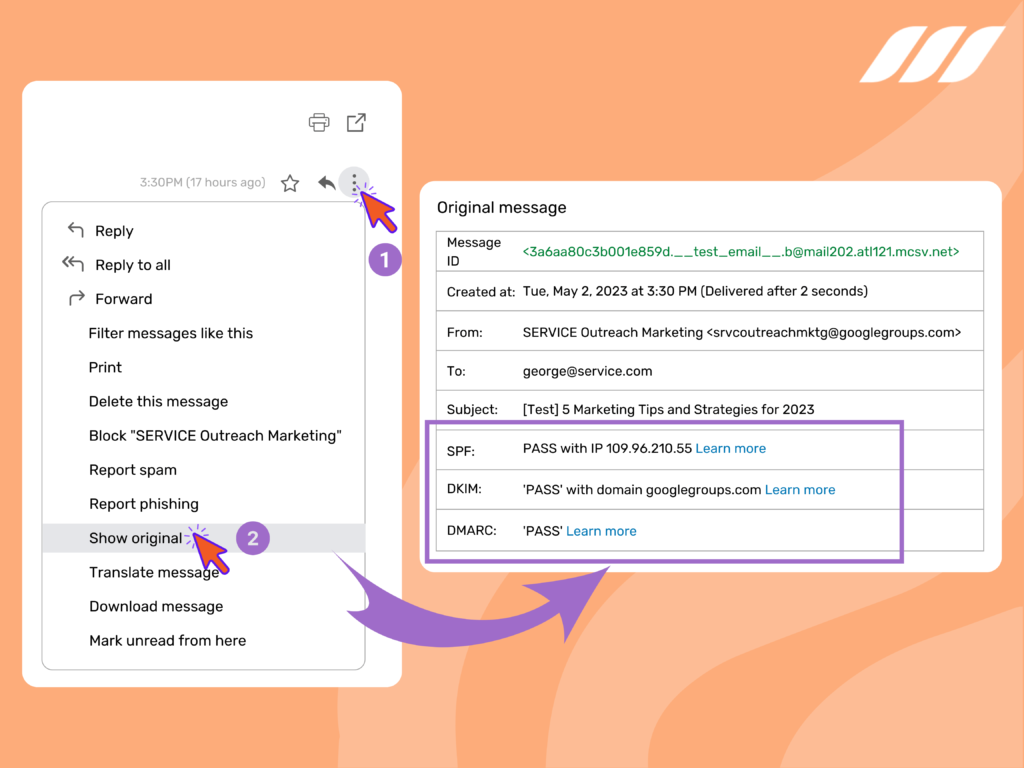
You can check whether an email has passed SPF, DKIM, and DMARC checks by looking at the email’s headers. Here’s how to do it:
- Open the email in your email client.
- Look for the email’s headers, which are usually hidden by default.
- Find the “Authentication-Results” header.
- Check the values of the SPF, DKIM, and DMARC fields to see if the email has passed the checks.
If an email fails any of the authentication checks, it may be marked as spam or rejected outright.
Setting up DMARC, DKIM, and SPF for a Domain
Setting up DMARC, DKIM, and SPF for a domain can be a complex process, but most email service providers offer step-by-step instructions on how to do it.
How to Set Up SPF
Navigate to your hosting website and find the DNS area; there, you’ll need to add a new record of the TXT type
In this screenshot, you’ll find the exact entries you’ll need to insert for the most common hosting providers:
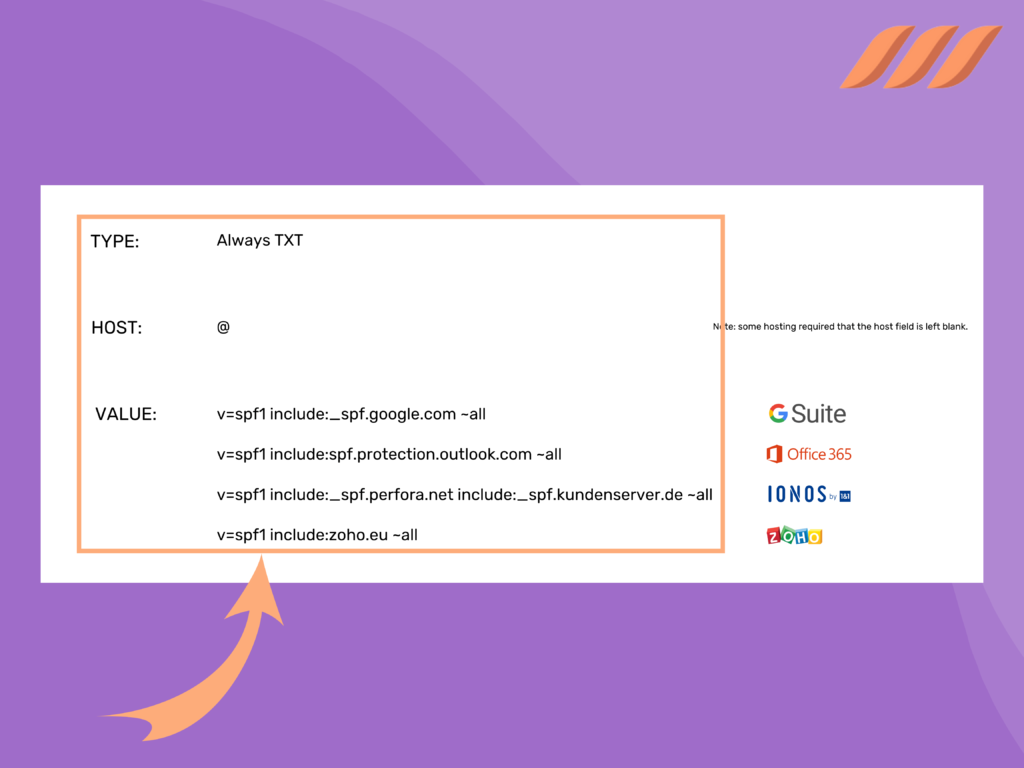
Record type: txt
Host: @
Value:
Gmail / G Suite v=spf1 include:_spf.google.com ~all
Office365 v=spf1 include:spf.protection.outlook.com ~all
IONOS v=spf1 include:_spf.perfora.net include:_spf.kundenserver.de ~all
ZOHO v=spf1 include:zoho.eu ~all
If you’re using some other email provider, please reach out to the support team for the exact record value.
Important things to note:
- Some hosting providers may have a separate section for the SPF records, but always remember to create the TXT type of record here.
- Do not have more than 1 SPF record installed in your hosting DNS section. In case you use multiple email servers, then include them in a single SPF record. As an example, the record for GSuite and Office365 going to look like this:
v=spf1 include:_spf.google.com include:spf.protection.outlook.com ~all.
How to Set Up DKIM
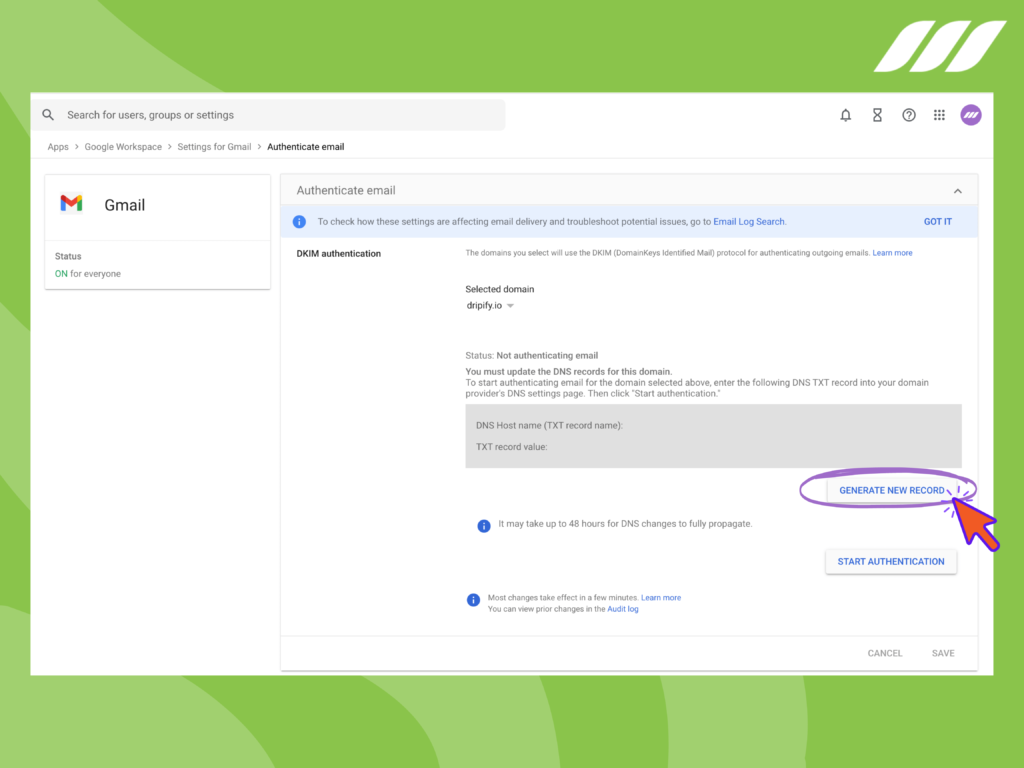
For Gmail / GSuite accounts, finding the DKIM record is super easy. Follow these steps to set up the DKIM record:
- Log into your gmail / G Suite account
- Go to Admin panel
- In the Search panel type DKIM to locate the DKIM settings page
- Click Generate New Record to create the record value
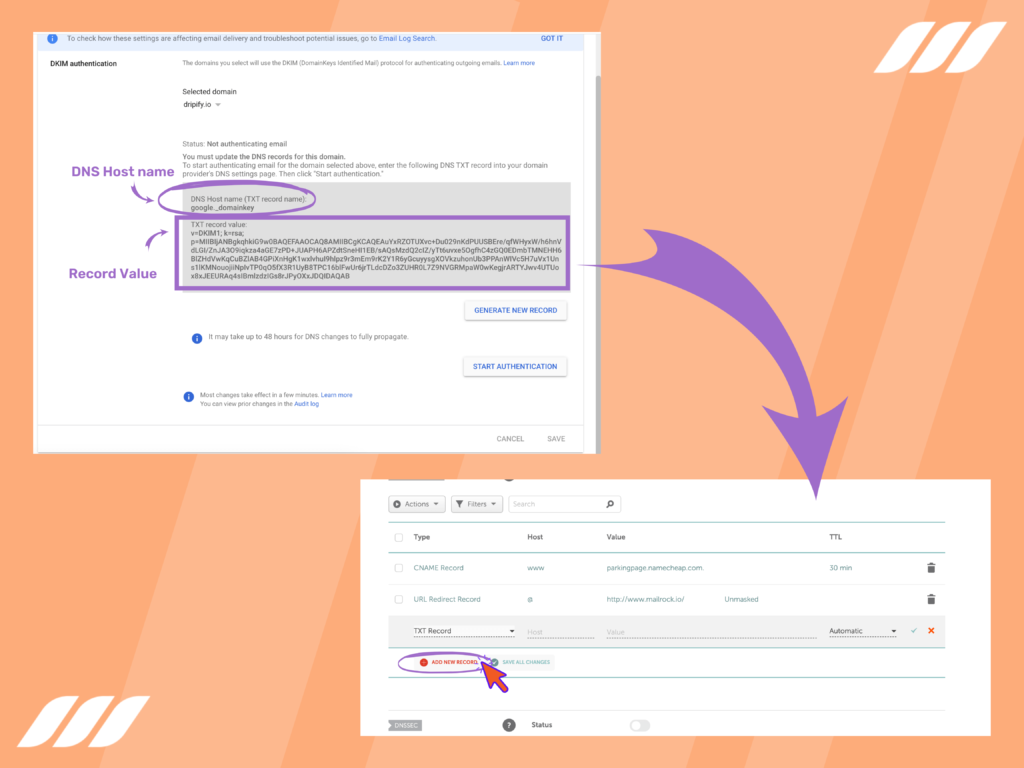
- Once completed you’ll get the txt record generated and displayed on this page. Copy the DNS Host name and Record value and create the txt record in the DNS page of your domain hosting:
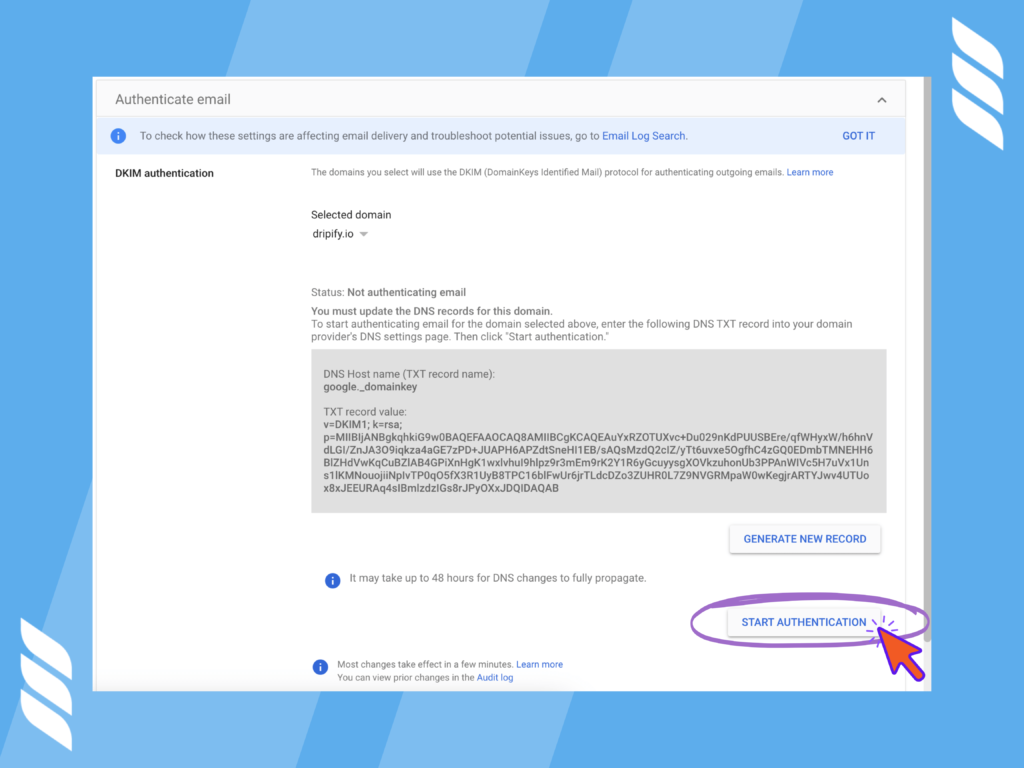
6. Once the txt record is added, go back to the DKIM settings page of GSuite and press Start Authentication to finish the process.
For other email providers, try to locate the DKIM settings page in the admin panel and generate the record there. In case you find any difficulties with that, reach out to the support team of the email provider for assistance.
How to Set Up DMARC Record
The DMARC record is the same for all email providers; thus, setting it up is easier than configuring the previous records.
To set it up:
- Log into your domain hosting and go to DNS settings
- Create a txt record with the following entries:
Type: TXT
Host: _dmarc
Value: v=DMARC1; p=none;
- Save the record, and the process is completed.
If you find the technical aspects of setting up these protocols difficult, consider asking your IT team for help. Or you may want to consult independent professionals who specialize in email authentication. They possess the necessary expertise to configure these protocols correctly and ensure their smooth operation.
IT experts can guide you through the process, including generating cryptographic keys for DKIM, configuring your email server or service provider, and adding the necessary DNS records for SPF, DKIM, and DMARC. They will ensure these protocols are properly integrated into your domain’s infrastructure and align with your organization’s specific requirements.
Also, remember that regular monitoring, analysis of reports, and ongoing maintenance are also crucial to ensure the effectiveness of these internet protocols for email authentication.
Use a Separate Domain for Cold Email Outreach
It’s always a good idea to use a separate domain for cold email outreach. Why? Because cold emails are more likely to be marked as spam, and using a separate domain can help protect your primary domain’s reputation.
Here are four reasons why it can be beneficial:
- Maintain Brand Reputation: Sending cold emails to potential prospects or clients can sometimes result in a higher risk of being marked as spam. By using a separate domain for cold emailing, you can mitigate the impact on your primary domain’s reputation.
If your cold emails generate many spam complaints or bounces, it won’t directly affect your primary domain’s deliverability or brand reputation. This separation allows you to safeguard your primary domain’s reputation for other critical email communications.
- Avoid IP Blacklisting: Sending a large volume of cold emails from your primary domain can potentially lead to your IP address being blacklisted by email service providers. This can severely impact your ability to deliver emails, including important customer communications.
Using a separate domain, you can isolate the potential risks of cold email outreach and protect your primary domain’s IP address from being blacklisted. This ensures that your regular business emails remain unaffected and maintain a high deliverability rate.
- Customize and Optimize: Having a dedicated domain for cold email outreach gives you more flexibility and control over the email-sending process. You can tailor the domain name to align with your cold email campaign or target audience.
Plus, you can optimize the domain’s reputation by gradually building a positive sending history and reputation specifically for cold emails. This allows you to implement specific email authentication protocols like SPF, DKIM, and DMARC to enhance deliverability and ensure your cold emails are trusted by recipients’ email providers.
- Analyze Performance Metrics: Using a separate domain for cold email outreach enables you to closely monitor and analyze the performance metrics of your cold email campaigns. You can track open rates, click-through rates, and cold email response rates, separate from your regular business emails. This valuable data can provide insights into the effectiveness of your cold email strategies, allowing you to make data-driven decisions, refine your campaigns, and improve overall outreach efficiency.
Related article: What Email Outreach Metrics to Track?
So, as you can see, a separate domain for cold outreach boosts the overall effectiveness and efficiency of your campaigns. By isolating your outreach activities to a distinct domain, you can maintain the pristine reputation of your primary domain, safeguarding it from potential deliverability issues that may arise from cold email practices.
Conclusion
Email authentication protocols like DMARC, SPF and DKIM are crucial for email marketers and businesses. These protocols work in tandem to enhance email security, improve deliverability, and protect brand reputation. Master email security with these protocols today to unlock the full potential of email marketing while ensuring a secure and trustworthy communication channel for your audience.
SPF verifies the authorized sending sources, DKIM adds a digital signature to validate the message’s integrity, and DMARC sets policies to handle failed authentication. Together, they form a powerful defense against spammers and protect recipients from phishing attempts. For email marketers, implementing these protocols means increased email deliverability, reduced spam filtering, and improved brand reputation.
![Email Outreach Tracking [Tips, Tricks and Tools]](https://dripify.io/wp-content/uploads/2025/02/11-7-png.avif)
![Create a Prospecting Plan [+8 Prospecting Methods]](https://dripify.io/wp-content/uploads/2025/02/11-png.avif)